A Burp Suite Beginners Tutorial
☰ Section: Security | ⚀ Posted: 2025-04-29 02:27:04 | ⚀ Updated: 2025-04-29 02:27:04 DALL-E via ChatGPT - powered by OpenAI
DALL-E via ChatGPT - powered by OpenAI
Mastering Web Security
In the ever-evolving landscape of web security, having the right tools is essential. Burp Suite is a powerful web application security testing toolkit and stands as an indispensable companion for security professionals, ethical hackers, and developers alike. This beginner friendly tutorial aims to guide you through the basics of Burp Suite, its key features, how to intercept traffic, and harness its capabilities to enhance the security of your web applications.
Whether you're new to web application security or preparing for your first bug bounty, mastering Burp Suite is a vital step in your journey. More than just a proxy, Burp Suite acts as a Swiss Army knife for ethical hackers, penetration testers, and developers seeking to understand and secure modern web applications. This beginner's guide will walk you through Burp Suite’s magic and help you understand how to test web requests, and explore vulnerabilities – all in a structured and intuitive way.
Introduction to Burp Suite
 PortSwigger.net
PortSwigger.net
What is Burp Suite?
Burp Suite is an integrated platform for web application security testing. It is developed by PortSwigger as a full featured Professional version, with advanced automation, scanning and plugin support, but also as a free Community Edition with limited features. Burp Suite is designed to identify vulnerabilities and potential security issues within web applications.
Burp Suite provides a comprehensive set of features for manual and automated testing, intercepting HTTP(S) traffic, and manipulating requests. It is widely used by web security professionals that do scanning for vulnerabilities, and automating repetitive tasks.
Installing Burp Suite
Download and Installation
- Visit the official Burp Suite website (https://portswigger.net/burp) to download the tool.
- Follow the installation instructions based on your operating system.
- Set up the necessary configurations, including proxy settings for your browser.
Installation on Kali Linux
- If it is not already installed in the tools collection, install it via APT.
- Open a terminal window via the keyboard shortcut
Ctrl + Alt + tand enter the following command on the Z-Shell. kali@kali ~% sudo apt install burpsuite
 m0rphisto.net
m0rphisto.net
Burp Suite Core Features
The Proxy
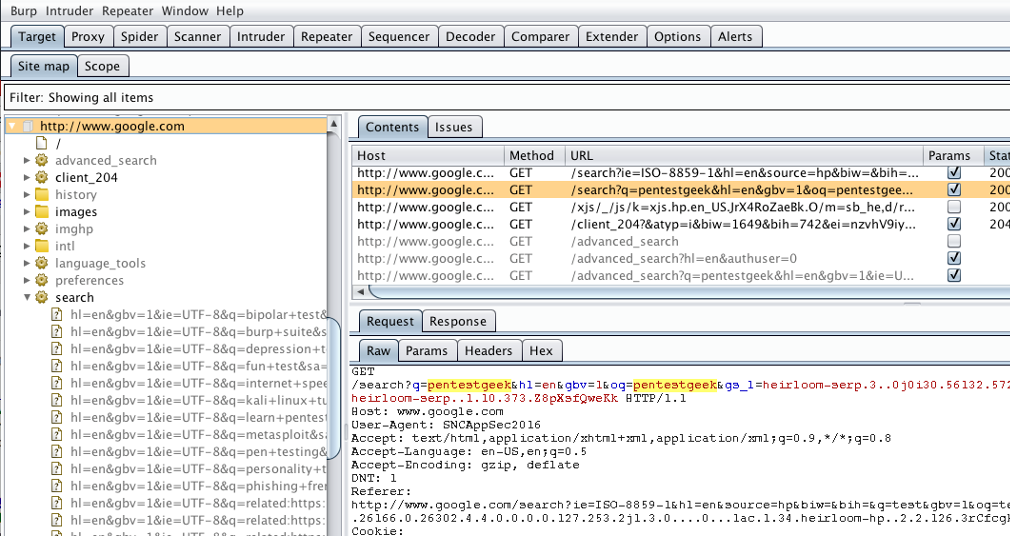
This is the heart of Burp Suite. It allows you to intercept, inspect, and also modify HTTP/S requests and responses between your browser and the target application.
How to Use It:- Toggle interception on/off in "Proxy" > "Intercept".
- Use "HTTP history" to view past requests.
- Modify parameters, headers, or cookies in real-time.
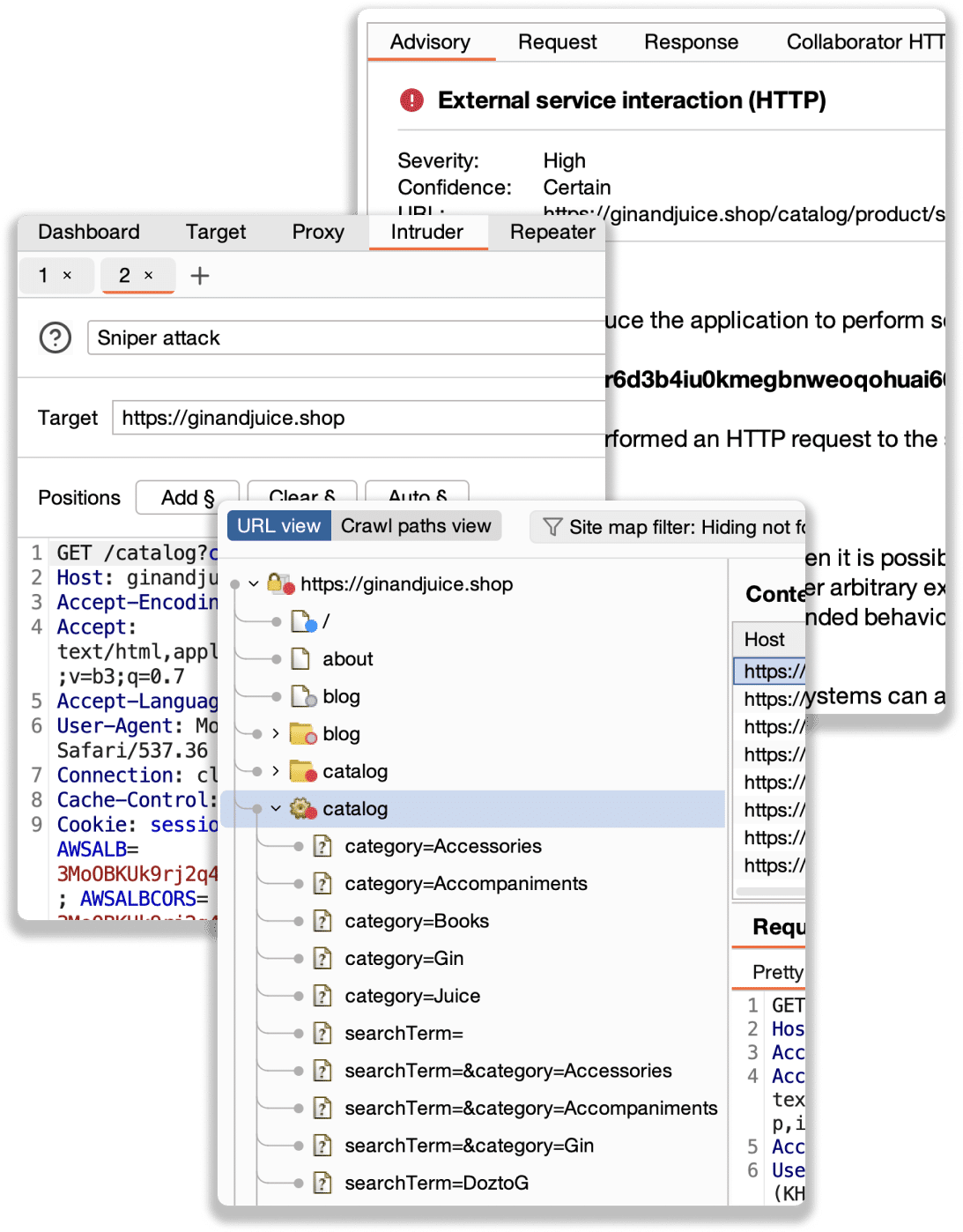
The Repeater
Repeater allows you to manually modify and resend individual HTTP requests to observe how the server sequentially responds. This is useful for testing different payloads or edge cases.
How to Use It:- Right-click any request in Proxy or HTTP history > “Send to Repeater”
- Modify the request body, headers, or method (GET, POST, etc.)
- Click "Send" and view the raw response.
 PortSwigger.net
PortSwigger.net
 PortSwigger.net
PortSwigger.net
Other useful tools
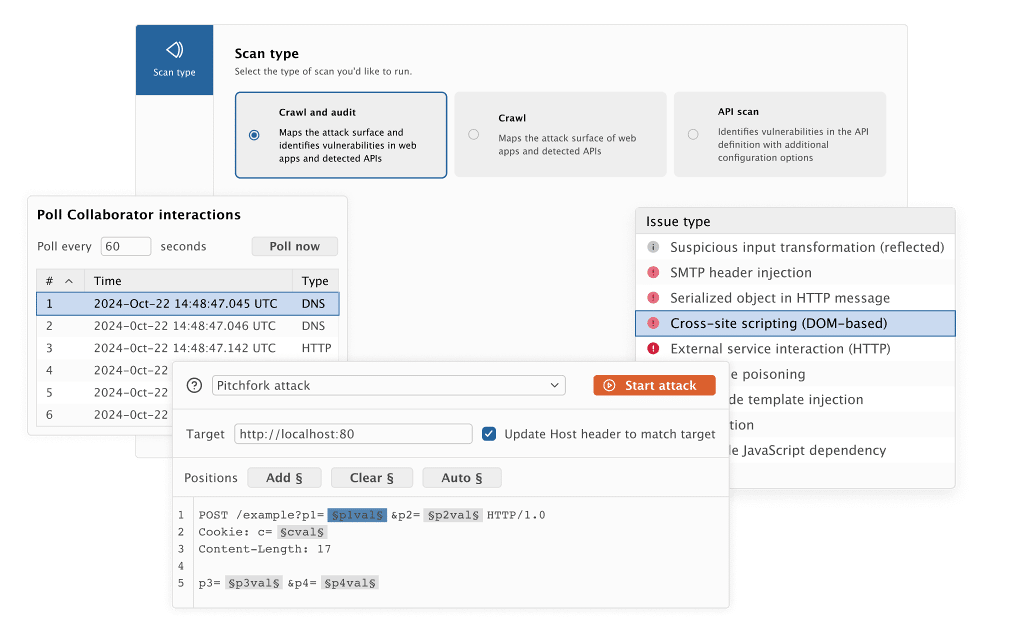
- Intruder: Automate attacks such as fuzzing or brute forcing.
- Scanner: Passive/active vulnerability scanner (pro version only)
- Decoder: Encode/decode base64, URL, hex, etc.
- Comparer: Diff responses or requests.
- Extender: Add Burp extensions or build your own.
Site Mapping
- Explore the Target tool to map the structure of a web application.
- Learn how to use site mapping for a better understanding of the application's functionality.
Getting Started with Burp Suite
Proxy Configuration
In order to get your browser working with Burp and intercept traffic, it acts as a local proxy at the loopback interface on the default proxy port. Default address is: 127.0.0.1:8080.
- Understand the role of Burp's Proxy tool in intercepting and modifying HTTP/S requests.
- Configure your browser to use Burp as a proxy or use the included version of Chromium.
- Learn to intercept and manipulate requests using Burp Proxy.
- Launch Burp and go to the "Proxy" > "Options" tab.
- Confirm the proxy listener is active on port 8080.
- Configure your browser (e.g., Firefox) to use 127.0.0.1:8080 as the HTTP and HTTPS proxy.
- Import Burp’s certificate into the browser to prevent SSL errors (via `http://burp` in the browser).
Practice Targets
Get hands-on by testing against deliberately vulnerable applications, but remember: If you have a running Kali GNU Linux these plattforms might be already installed or are installable via apt, the advanced package manager.
- [DVWA] (https://sourceforge.net/projects/dvwa.mirror/)
- [bWAPP] (https://sourceforge.net/projects/bwapp/)
- [OWASP Juice Shop] (https://owasp.org/www-project-juice-shop/)
- [TryHackMe Labs] (https://tryhackme.com/room/burpsuiterepeater)
- [Hack The Box Labs] (https://academy.hackthebox.com/course/preview/using-web-proxies)
Another way leads you to specifically developed virtual machines running under VirtualBox. A very good application giving the possibility to simulate complete network structures.
- [VulnHub] (https://vulnhub.com/)
- [TheMatrixVM] (https://sourceforge.net/projects/thematrixvm/)
- [WebsecurityDoJo] (https://sourceforge.net/projects/websecuritydojo/)
Scanning and Analysis
Automated Scanning
- Discover how to use Burp's automated scanning capabilities to identify common vulnerabilities.
- Configure scan settings and analyze scan results.
Manual Testing
- Dive into manual testing techniques using the Repeater and Intruder tools.
- Understand how to identify and exploit vulnerabilities through manual testing.
Advanced Features
Session Handling
- Explore Burp's session handling capabilities to manage authentication and session-based security mechanisms.
Extensibility
- Learn about Burp Extender and how to leverage extensions for customizing and extending Burp's functionality.
Best Practices and Tips
Configuration Tips
- Optimize Burp Suite configurations for efficiency and accuracy.
- Explore various settings and customization options.
- Take notes on what each parameter does.
- Learn keyboard shortcuts for faster navigation.
- Use the Burp Suite Documentation & PortSwigger Web Security Academy.
- Practice regularly – Burp is powerful, but it takes time to master.
Collaborative Work and Security Ethics
As you continue to explore and master Burp Suite, always remember to prioritize ethical hacking practices and responsible disclosure for a safer and more secure digital landscape. Never forget: Breaking into computers or networks is illegal!
Even the attempt is considered a crime.- Understand the reporting features in Burp Suite.
- Learn how to generate comprehensive reports for stakeholders.
- Explore collaboration features to share findings and collaborate with team members.
Wrapping Up
Burp Suite is a versatile and powerful tool that can significantly enhance your web application security testing capabilities. This tutorial provides a foundational understanding of Burp Suite's key features, enabling you to conduct thorough security assessments and contribute to the creation of robust, secure web applications.
Burp Suite is more than a tool – it's an environment to deeply understand web traffic, test security boundaries, and learn ethical hacking by doing. With practice, the proxy and repeater will become second nature, and you’ll uncover vulnerabilities that would otherwise go unnoticed.
Got it all figured out? You've got the full picture? Alright, let's go - happy hacking!
Have lot of Fun ...
.m0rph
-----BEGIN GEEK CODE BLOCK----- GIT e+ d-- s++:++ a++ G++ C+++ M-- W+++ L++++>$ P+++ E--- W+++ N++ o+ PS+++ PE+++ Y++ PGP++ !DI t++ 5-- X++ R++ tv- b-(++) h+ r- y(++)- -----END GEEK CODE BLOCK-----