The Difference Between SSO Passwords and One-Time Passwords Explained
☰ Section: Security | ⚀ Posted: 2025-04-29 02:27:04 | ⚀ Updated: 2025-04-29 02:27:04 DALL-E via ChatGPT - powered by OpenAI
DALL-E via ChatGPT - powered by OpenAI
Understanding One-Time Passwords and Single Sign-On
In today's digital world, secure access to online services is more important than ever. With countless apps, platforms, and systems requiring authentication, it's easy to get overwhelmed by the various methods used to protect our identities. Two common yet often misunderstood terms in this space are Single Sign-On (SSO) and One-Time Passwords (OTP). Although they both aim to simplify and secure the login process, they serve entirely different purposes and operate in distinct ways.
This article is designed to clear up the confusion. Whether you're a developer, IT professional, or simply someone curious about how authentication works, you'll find a straightforward explanation of SSO and OTP – including their differences, use cases, and how they impact both security and user experience.
So what is an OTP?
One-Time Passwords are dynamic, time-limited passwords that are valid for one single login only. They are often used as an additional security layer (Multi-Factor Authentication) and are typically generated via SMS, eMail, or through an authenticator app. SSO generally does not use one-time passwords as the primary login method. The very goal of SSO is to authenticate just once with your regular credentials (i.e., the SSO password). However, OTPs can be used additionally within an SSO process to enhance security.
And what is an SSO?
Single Sign-On indeed means "logging in once". It's an authentication method that allows a user to log in with a single set of credentials (username and password, or other authentication methods) to access multiple independent software systems. SSO passwords are therefore used within a Single Sign-On system to authenticate once and then gain access to several applications or services.
What sense would it make to steal SSO passwords?
Stealing SSO passwords can be very valuable!
The attackers get ...
access to multiple systems:A compromised SSO password allows attackers to log in to all applications and services connected to that SSO system. It's a "key to many doors."
facilitated lateral movement:Within an organization, attackers who have taken over an SSO account can move more easily through different systems, access sensitive data, and launch further attacks under another identity.
high values in cash:Stolen SSO credentials can be traded on the dark web and misused for various criminal activities.
Aren't SSO passwords created "on the fly"?
No, unfortunately not! SSO passwords are are static passwords that the user (or in some cases, an administrator) sets and ideally is stored and managed securely.
The authentication process for SSO works more like this:
- The user tries to access an application.
- The application redirects the user to the SSO identity provider.
- The user authenticates there with their SSO password (and possibly additional factors like an OTP).
- Upon successful authentication, the identity provider issues a "ticket" or "token" that the application can validate to grant the user access without them having to log in again.
The alleged Oracle™ hack
Even if the passwords were encrypted, the theft poses a significant risk.
Reports about the alleged hack at Oracle™ indicate that encrypted SSO passwords and other sensitive data like JKS files (Java Keystore) and Enterprise Manager JPS keys were indeed stolen.
- Decryption attempts:Attackers could try to decrypt the passwords through brute-force attacks or other methods, especially if the encryption is weak or if the associated keys were also compromised (as suggested by the theft of the JPS keys).
- Exploitation of other compromised data:The stolen JKS files and keys could allow attackers to decrypt other sensitive configuration files that, for example, contain database access credentials.
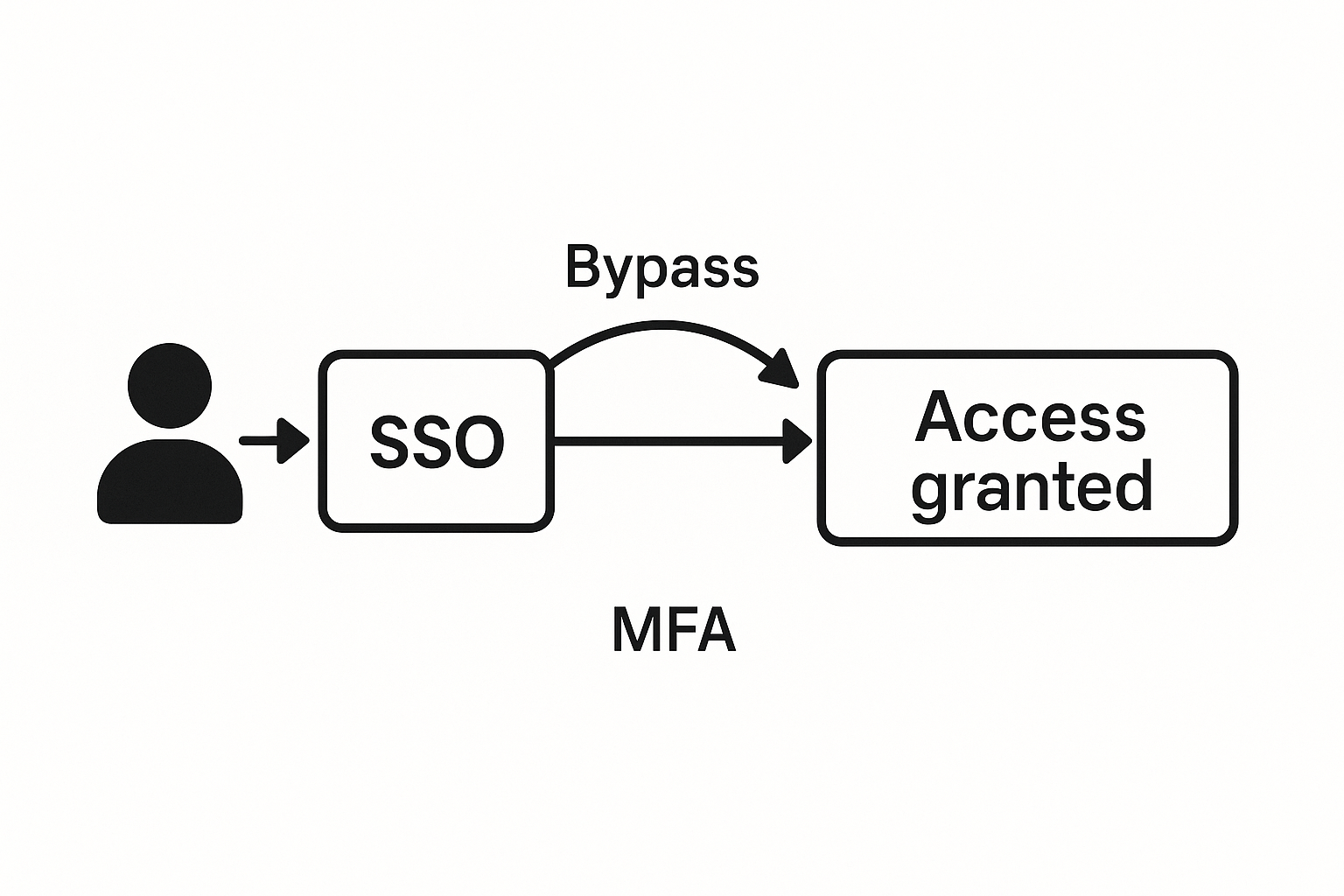
- Bypassing authentication mechanisms:With the stolen and potentially decrypted data, attackers might be able to bypass authentication mechanisms and log into various cloud systems unnoticed.
It's important to emphasize that Oracle™ initially denied the incident, but there are now reports that customers have been informed about the data theft. The exact impact and the nature of the stolen "SSO passwords" (whether they are directly usable hashes or other sensitive authentication information) are still subject to further investigation and information.
 ChatGPT - powered by OpenAI
ChatGPT - powered by OpenAI
Got some light into the dark? I hope this explanation helps you understand the connections better!
Have lot of Fun ...
.m0rph
-----BEGIN GEEK CODE BLOCK----- GIT e+ d-- s++:++ a++ G++ C+++ M-- W+++ L++++>$ P+++ E--- W+++ N++ o+ PS+++ PE+++ Y++ PGP++ !DI t++ 5-- X++ R++ tv- b-(++) h+ r- y(++)- -----END GEEK CODE BLOCK-----